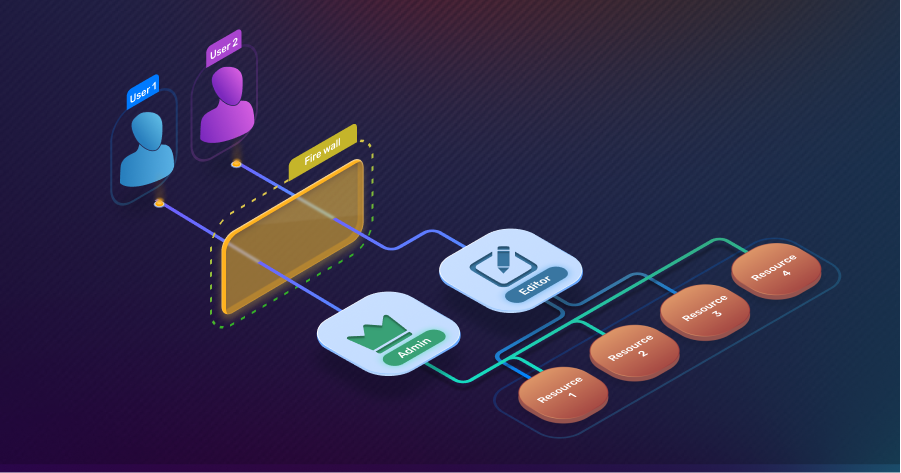
In today’s digital world, securing our data is more important than ever. One of the most effective ways to do this in applications is by using Role-Based Access Control (RBAC). This method is used to manage what different users can do within a system. For example, think of a school where students, teachers, and administrators all have different roles. Each group has certain tasks they can perform based on their role. This is exactly how RBAC works in full stack applications.
For those learning web development in a full stack developer course in Bangalore, RBAC is a crucial concept. It helps developers understand how to build secure applications and ensure that users only have access to what they need. Let’s break down how RBAC works, why it’s important, and how developers can implement it in their projects.
What is Role-Based Access Control (RBAC)?
RBAC is a way to restrict access to certain parts of an application based on a user’s role. In simpler terms, it means that users are assigned specific roles, and each role has permissions attached to it. These permissions determine what users can see and do within an application.
For example, in an online bookstore, a customer can browse books and place orders, while an admin can manage inventory, add new books, or handle user queries. These actions are controlled by assigning different roles (like customer or admin) to each user, ensuring they only have access to the parts of the system that are relevant to them.
Why is RBAC Important in Full Stack Development?
RBAC is important because it helps protect sensitive data and limits the actions a user can take within an application. For instance, in a banking application, regular users should only see their account details, while bank employees might need access to broader information. If an unauthorized user were to access sensitive data, it could lead to serious security issues. This is why implementing RBAC is essential for developers building secure applications.
In a full stack developer course in Bangalore, students often learn how to implement RBAC to ensure their applications are safe from potential breaches.
How RBAC Works in Full Stack Applications
RBAC can be applied in both the front-end and back-end of a full stack application. Here’s how it works:
- Roles and Permissions: First, developers define the different roles (like admin, editor, or viewer) and what actions each role can perform. These permissions could be anything from viewing a webpage to editing or deleting data.
- Assigning Roles to Users: Once the roles and permissions are set, developers assign users to specific roles based on their needs. For example, in an online classroom app, a teacher might be assigned the role of “instructor,” while students have the role of “learner.”
- Restricting Access: Based on the assigned roles, users are restricted from accessing features that aren’t relevant to them. This is done both on the front-end (what users can see) and the back-end (what users can do on the server).
Implementing RBAC: A Step-by-Step Approach
Implementing RBAC in a full stack application involves a few key steps. Here’s a simple guide for beginners:
1. Define Roles and Permissions
Start by listing the roles your application will need. For example, in an online store, you might have these roles:
- Customer: Can browse products, add items to the cart, and make purchases.
- Admin: Can add, update, or delete products, manage orders, and handle customer queries.
Next, define what each role can do. For instance:
- Customer: View products, and place orders.
- Admin: Manage products; and view all orders.
2. Assign Users to Roles
Once the roles are defined, users need to be assigned a role when they sign up. This could be done through a registration form or by an admin managing the system.
3. Restrict Access Based on Roles
With users assigned roles, the application should now check their role before allowing access to certain features. For example:
- On the front-end, hide buttons or links that the user shouldn’t see. For instance, a customer should not see the “Manage Products” button that only admins can access.
- On the back-end, verify user roles before performing any database operations. This makes sure that even if a user tries to access restricted areas, the system won’t allow it.
4. Test for Security
After implementing RBAC, always test it thoroughly. Make sure that users with restricted roles can’t access sensitive parts of the application by accident. This helps in finding any loopholes in your system.
Example: RBAC in a School Application
Let’s imagine a school management app that has three types of users: students, teachers, and administrators. Here’s how RBAC could be set up:
- Student: Can view their grades, check homework, and submit assignments.
- Teacher: Can post homework, grade assignments, and view student progress.
- Administrator: Can manage user accounts, view all data, and update class schedules.
In this app, students shouldn’t have access to grading tools, and teachers shouldn’t be able to change user accounts. RBAC ensures that each group of users can only perform actions specific to their role, keeping the system organized and secure.
Challenges in Implementing RBAC
While RBAC is highly effective, it does come with some challenges:
- Role Explosion: If an application has too many roles, managing permissions can become complicated. This is called “role explosion,” and developers need to avoid creating too many overlapping roles.
- Keeping Permissions Updated: Over time, as applications evolve, permissions may need to be updated. Developers must ensure that these changes are properly managed.
- Scalability: As applications grow, ensuring that RBAC scales properly with more users and roles can become difficult. Developers need to design RBAC systems that are flexible and can handle growth.
How Full Stack Developer Classes Can Help
Full stack development is a complex field, and learning to implement RBAC is a crucial part of building secure and functional applications. A full stack developer course equips students with the knowledge and hands-on experience needed to build applications with strong security features like RBAC. In these courses, students learn how to define roles, assign permissions, and enforce access control in real-world projects.
By mastering RBAC, students will be better prepared to tackle security challenges in their careers and create applications that protect users’ data.
Conclusion
RBAC is an essential security feature in full stack applications. By controlling user access based on roles, developers can make sure that their applications stay secure and efficient. For those interested in becoming developers, learning to implement RBAC is a valuable skill, especially in a full stack developer course, where students gain the tools needed to succeed in the tech industry.
Understanding and applying RBAC can make the difference between a vulnerable app and a secure one, and it’s a skill every aspiring developer should master.
Name: ExcelR – Business Analyst, Full Stack Development, Tableau & Power BI Course Training
Address: 10, 3rd floor, Safeway Plaza, 27th Main Rd, Old Madiwala, Jay Bheema Nagar, 1st Stage, BTM 1st Stage, Bengaluru, Karnataka 560068
Phone: 07353006061
Business Email:enquiry@excelr.com


